In today's interconnected world, managing IoT devices securely is more important than ever. SSH login for IoT devices on Mac has become a critical skill for professionals and enthusiasts alike. Whether you're setting up home automation systems or managing industrial IoT devices, understanding how to use SSH effectively is essential. This guide will walk you through everything you need to know about SSH login for IoT devices on Mac, ensuring your devices remain secure and efficient.
As technology advances, the number of IoT devices continues to grow exponentially. According to a report by Statista, there were over 14 billion IoT devices worldwide in 2023, and this number is expected to surpass 25 billion by 2030. With such rapid growth, the need for secure communication between devices has become paramount. SSH (Secure Shell) provides a robust solution for managing these devices remotely.
This article is designed to help you understand the fundamentals of SSH login for IoT devices on Mac, explore best practices, and equip you with the knowledge to troubleshoot common issues. Whether you're a beginner or an experienced user, this guide will serve as a valuable resource for all your SSH-related needs.
Read also:Exploring The Life Of Isabella Rose Giannulli A Journey Through Fame Family And Fashion
Table of Contents
- Introduction to SSH
- Why SSH Is Important for IoT
- Setting Up SSH on Mac
- Connecting to IoT Devices
- Best Practices for SSH
- Security Tips for SSH
- Troubleshooting Common Issues
- Using SSH Keys
- SSH Alternatives for IoT
- Future of SSH in IoT
- Conclusion
Introduction to SSH
SSH, or Secure Shell, is a cryptographic network protocol designed for secure communication between devices. It provides a secure way to access remote servers and devices, making it an ideal tool for managing IoT devices. SSH ensures data integrity, confidentiality, and authentication, which are critical for maintaining the security of IoT networks.
One of the primary advantages of SSH is its ability to encrypt data transmitted between devices, preventing unauthorized access and eavesdropping. This encryption makes SSH a preferred choice for managing IoT devices on Mac, where security is a top priority.
Why SSH Is Important for IoT
In the realm of IoT, security is a major concern. IoT devices often lack robust security features, making them vulnerable to attacks. SSH login for IoT devices on Mac addresses this issue by providing a secure channel for communication. By using SSH, you can ensure that your IoT devices remain protected from unauthorized access and malicious activities.
Furthermore, SSH simplifies the management of IoT devices by allowing remote access and control. This is particularly useful for devices located in remote locations, where physical access may not always be feasible. With SSH, you can manage your IoT devices from anywhere, ensuring they remain operational and secure.
Setting Up SSH on Mac
Installing SSH
Mac comes with SSH pre-installed, so there's no need for additional installations. However, you may need to enable SSH in your system preferences. To do this, follow these steps:
- Open System Preferences on your Mac.
- Click on Sharing.
- Select Remote Login from the list of services.
- Ensure the checkbox for Remote Login is enabled.
Configuring SSH
Once SSH is enabled, you can configure it to suit your needs. This involves setting up user permissions, specifying allowed IP addresses, and configuring encryption settings. For advanced users, you can also modify the SSH configuration file located at /etc/ssh/sshd_config.
Read also:Quad Witching A Comprehensive Guide To Understanding The Market Phenomenon
When configuring SSH, it's important to follow best practices to ensure maximum security. This includes using strong passwords, enabling two-factor authentication, and regularly updating your system to patch any security vulnerabilities.
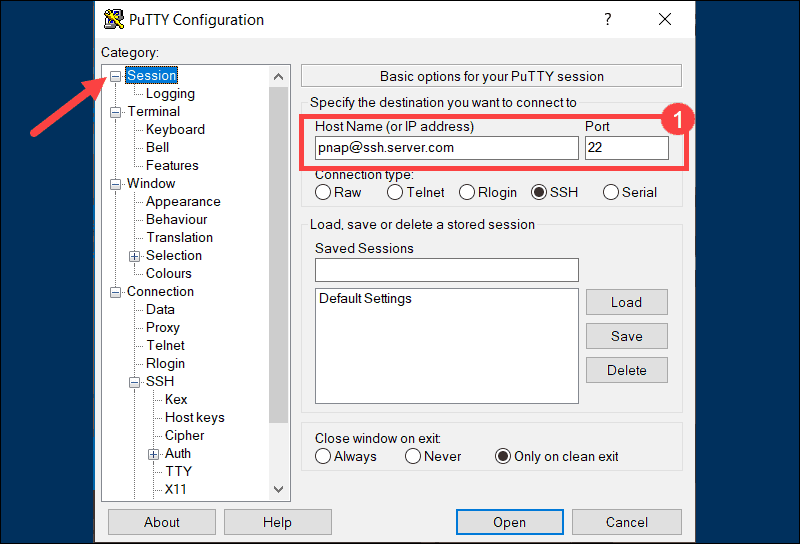
Connecting to IoT Devices
Connecting to IoT devices using SSH on Mac is a straightforward process. You can use the Terminal application to establish a connection. Simply open Terminal and type the following command:
ssh username@device_ip_address
Replace "username" with your IoT device's username and "device_ip_address" with the IP address of your IoT device. If the connection is successful, you will be prompted to enter your password. Once authenticated, you will have access to your IoT device's command-line interface.
Best Practices for SSH
To ensure the secure and efficient use of SSH for IoT devices on Mac, it's important to follow best practices. These include:
- Using strong, unique passwords for each device.
- Enabling two-factor authentication for added security.
- Regularly updating your SSH client and server software.
- Limiting access to trusted IP addresses only.
- Monitoring SSH logs for suspicious activities.
By adhering to these best practices, you can minimize the risk of security breaches and ensure your IoT devices remain secure.
Security Tips for SSH
In addition to best practices, there are several security tips you can follow to enhance the security of your SSH setup. These include:
- Using SSH keys instead of passwords for authentication.
- Disabling root login to prevent unauthorized access.
- Changing the default SSH port to a non-standard port.
- Implementing firewall rules to restrict access.
- Regularly reviewing and updating your security policies.
Implementing these security tips will help protect your IoT devices from potential threats and ensure they remain secure and operational.
Troubleshooting Common Issues
While SSH is a robust protocol, you may encounter issues when connecting to IoT devices on Mac. Common problems include connection timeouts, authentication failures, and configuration errors. To troubleshoot these issues, you can try the following:
- Verify the IP address and port number of your IoT device.
- Check your network settings to ensure connectivity.
- Review your SSH configuration file for errors.
- Restart your SSH service and try connecting again.
- Consult the documentation for your IoT device for troubleshooting tips.
If the issue persists, you may need to seek assistance from your device's manufacturer or consult online forums for additional support.
Using SSH Keys
SSH keys provide a more secure alternative to passwords for authentication. By using SSH keys, you can eliminate the need for passwords, reducing the risk of brute-force attacks. To set up SSH keys, follow these steps:
- Generate a key pair using the ssh-keygen command.
- Copy the public key to your IoT device using the ssh-copy-id command.
- Test the connection to ensure the key is working correctly.
Using SSH keys not only enhances security but also simplifies the login process, making it faster and more convenient.
SSH Alternatives for IoT
While SSH is a popular choice for managing IoT devices, there are other protocols you can consider depending on your needs. Some alternatives include:
- MQTT: A lightweight protocol designed for IoT devices with limited resources.
- CoAP: A protocol designed for constrained networks and devices.
- HTTP/HTTPS: A widely used protocol for web-based communication.
Each protocol has its own advantages and disadvantages, so it's important to choose the one that best suits your requirements.
Future of SSH in IoT
As IoT continues to evolve, the role of SSH in managing IoT devices will become increasingly important. With the growing number of connected devices, the need for secure communication protocols will only increase. SSH is well-positioned to meet this demand, thanks to its robust security features and ease of use.
In the future, we can expect to see advancements in SSH technology, such as improved encryption algorithms, enhanced key management, and better integration with IoT platforms. These developments will further solidify SSH's place as a critical tool for managing IoT devices on Mac.
Conclusion
In conclusion, mastering SSH login for IoT devices on Mac is essential for anyone involved in managing IoT networks. This guide has provided you with a comprehensive understanding of SSH, its importance in IoT, and how to set it up and use it effectively. By following best practices and security tips, you can ensure your IoT devices remain secure and operational.
We encourage you to share your thoughts and experiences in the comments section below. Your feedback will help us improve this guide and provide better resources for our readers. Additionally, feel free to explore other articles on our site for more valuable insights into IoT and related technologies.